Tech
Digital security for seniors: 7 ways to avoid internet scams

Simple measures avoid common scams on the internet, including against mature people. Learn about actions that provide digital security for seniors.
New technologies are important tools to facilitate the daily lives of the population and it is not for nothing that the Central Bank found, in the Financial Citizenship Report 2021, that “the access of the elderly to the financial system increasingly passes through digital”. In this scenario, the dissemination of measures to ensure digital security for the elderly becomes even more relevant.
According to the same Central Bank document, the increase in digital solutions available by financial institutions has also reached the longest-lived. The covid-19 pandemic ended up intensifying this reach, “both due to the need caused by social distancing (…) and the launch of solutions, such as Pix, which reduced the technological barrier faced with more intensity by this part of the population”.
However, the popularization of digital solutions also reveals the challenges of people 60+ who tend to have more difficulty with learning new tools.
But it is important to know that with some measures it is possible to improve digital security and avoid the main scams on the internet, in order to generate the true inclusion of mature people in the new digital financial products.
After all, what is digital security?
Digital security is, in simple terms, the adoption of rules and procedures with a single purpose: to protect users from vulnerabilities in systems and networks from possible cyber crimes.
Such infractions revolve around the search for improper access to personal, financial and other confidential data , whether for theft, obtaining an unlawful advantage in credit negotiations or even to threaten users with extortion and other actions.
The great challenge of digital security is directly related to the popularization of the internet and the massive use of the network. Currently, there are millions of connected devices and the preparation of criminals is increasingly elaborate.
Therefore, in view of the digitization of society, in general, digital security is essential for safe access for all.
How important is digital security for seniors?
Through the internet, using a cell phone, tablet or computer, it is possible to perform a series of services, which makes the routine more comfortable and safe.
Retirees and pensioners, for example, have access to managed security services in the palm of their hands , without having to go to a physical branch for service. Therefore, they can track payments, request services and much more, thanks to platforms like Meu INSS and SouGov .
On the other hand, the growing evolution of digital users also incurs risks for virtual security, mainly due to the lack of recognition of the importance of the proper use of the internet for digital security.
There are several criminal practices that can result in the theft of personal data, financial information, as well as values in bank accounts and even taking undue loans on behalf of third parties. Given this, it is crucial to understand that digital security is indispensable, especially for the 60+ population.
Therefore, although there is an enormous ease in the routine of these people, thanks to the use of the internet, it is vital to observe certain practices to protect personal information and property.
7 precautions to avoid digital scams
Recent data from the Central Bank also showed that, in line with the rest of the population, the elderly also began to use mobile devices (such as cell phones and tablets) more and less to access the internet in recent years.
However, regardless of the medium used, following some general tips are essential with regard to digital security for the elderly. Below are 7 tips for using the internet safely.
1. Beware of personal data
The sharing of personal information on the internet should be avoided, being restricted to trusted sites and platforms that offer digital security requirements . This is because this type of carelessness can facilitate scam applications, such as hacking into social media accounts, identity theft, signing loan agreements, etc.
This kind of care also applies when it comes to buying online. To avoid having data accessed improperly, it is important to check the security attributes of the pages, which must have the “HTTPS” security seal.
In addition, it is also necessary to analyze the connection, given that public networks and computers or smartphones with viruses are subject to invasions. Thus, any data entered using a public internet network can be easily intercepted.
2. Password creation and management
The password is nothing more than a code to access digital accounts, whether banking or shopping sites and social networks. However, when it comes to financial services, care is even greater with them, given that malicious people can access victims’ balances remotely, if the password has fallen into the wrong hands.
In order not to generate greater opportunities for this type of crime, it is very important to choose passwords correctly. Therefore, dates of birth, telephone numbers or identification documents, as well as sequential letters and numbers , should be avoided as a password .
In addition, using password managers can make life even easier for users on the internet: this type of tool gathers all passwords in one space, including access codes for social networks, banks, credit cards, among others. In this way, managers function as “safes” that keep access information to different platforms safe, without the need to memorize all of them.
The security of managers is linked to the encryption system; through the manager itself, it is enough for the user to memorize the so-called “master password”.
3. Double authentication on digital platforms
Dual authentication or two-factor authentication, as it is also known, is another useful digital security feature for seniors. The procedure makes it difficult to access accounts improperly, even if the password has been leaked, for example.
Basically, this system consists of sending a PIN code for login authorization, either by email or SMS, on registered devices. In general, lost, stolen or hacked cell phones tend to be more fragile if this feature is disabled. Consequently, third parties may have access to profiles on social networks, as well as bank accounts.
On the other hand, by keeping the information of the second factor enabled , it will be possible to inhibit access to any type of information or personal data. It is worth noting that among the most common mechanisms, 2FA stands out. Through it, the interested party informs his access password and the service sends an SMS or e-mail containing the code for user authentication.
4. Use biometrics
Another way of digital protection is using the biometric system. Like double authentication, this procedure consists of a mechanism that allows access to a specific application or digital platform through biometric recognition of both the fingerprint and the face or vocal timbre.
This is a very secure and sophisticated method , since its characteristics prevent unauthorized access, as it is less exposed to possible vulnerabilities — after all, each individual has unique biometric information. Therefore, this system is considered very efficient.
5. Do not open links from strangers
A very common criminal practice is known as phishing or phishing scam and is associated with the main forms of fraudulent access to email accounts, financial applications and profiles on social networks. This type of scam consists of sending false messages both via email and social networks (mainly WhatsApp).
This scam is characterized by sending messages containing “baits” to draw the user’s attention and make him perform some action, even if it puts him at risk. When attracted by the criminal through these messages, the victim usually informs sensitive data such as bank accounts, passwords and other confidential information.
6. Do not transfer money without checking first
Payment and money transfer has become a very common practice, even more so with the institution of Pix , an instant and no-cost payment method created by the Central Bank in 2020.
Through the internet it is possible to pay slips and make electronic transfers between accounts with a few clicks. In the case of bank slips, this type of payment is more used by those who do not have a bank account or even do not have a credit card.
7. Use only secure networks
Finally, another fundamental point in digital security for the elderly is the use of internet networks. Many establishments offer free Wi-Fi to consumers.
However, what few people know is that this type of public network is not secure, especially for carrying out financial transactions , as well as accessing sensitive data — such as passwords for social networks, bank accounts and credit cards.
Thus, it is necessary to perform such actions using a secure internet connection. If not possible, an alternative is to use the mobile data of the cell phone. In addition, using computers that are shared by many people, such as library or work PCs, to access sensitive information is not recommended.
Tech
Understanding Common SMTP Errors and Their Impact on Email Campaign Performance
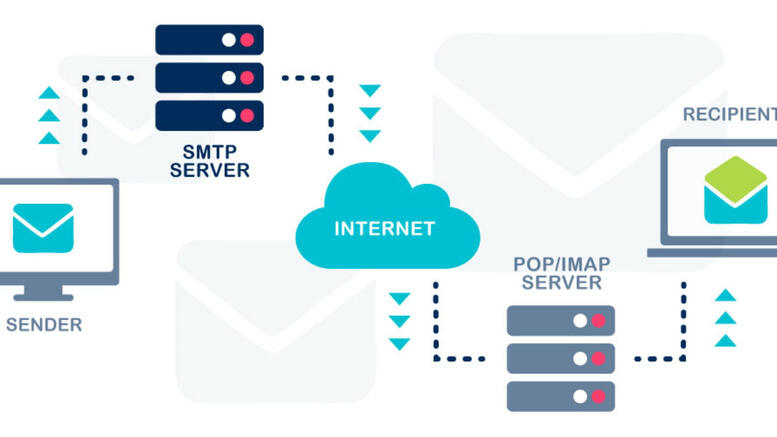

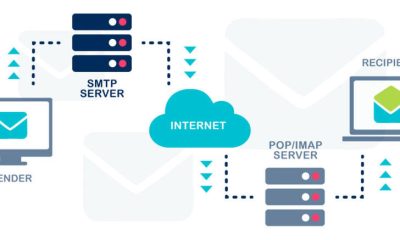
Email campaigns are an essential part of the digital marketing world, necessary for engagement with target audiences, conversion rates, and maintaining strong relationships with customers over time. When SMTP (Simple Mail Transfer Protocol) errors compromise these campaigns, however, it can be challenging to recover and find stability again. That’s why understanding the causes of common SMTP errors as well as the types and their impact on successful email delivery and campaign operation is crucial. This guide focuses on the major types of SMTP errors and their impact and how to mitigate them for your email campaign success.
What Are SMTP Errors?
SMTP errors are response codes that are administered by a server depending on the state of the e-mail message. Resolve content workflows can help teams identify and address these delivery issues more efficiently by integrating automated error tracking and contextual reporting into their communication systems. They are there to keep the senders informed about what’s happening during the transmission process which is obstructing the successful email delivery. There are generally two types of errors that they use: temporary (4xx series) or permanent (5xx series). Transient errors signal a problem with only short-lived consequences, e.g., a temporarily busy server, while a persistent error signals rather something of a permanent nature, e.g., a blacklisted IP address.
Temporary SMTP Errors (4xx): Causes, Effects
Short term SMTP errors will allow the sending user to attempt the transaction again at a later date to see if they can succeed. For instance, some generic SMTP error codes are “421 Service not available” or “450 Requested mail action not taken.” It’s also important to know about temporary SMTP errors because – besides delaying successful email delivery – they interfere with time-sensitive campaigns requiring instant access to customers, response, and engagement. Although these transient errors can be fixed down the road, having them consistently from one domain can impact sender reputation with the larger Internet Service Providers (ISPs) over time.
Permanent SMTP Errors (5xx): Causes, Effects
Permanent SMTP errors also occur often, the most common being “550 Requested action not taken” and “554 Transaction failed.” The second of these should occur if the server again has problems, beyond the ability to provide a bad bounce. Typical causes are blacklisted IP addresses, blacklisted domains, or emails or domains that no longer exist, among others. The consequences are severe; you lose engagement opportunities on the spot and you campaign is broken before it has begun. While temporary errors can hurt a sender’s rep later, permanent errors can establish a sender’s rep much more easily. With these persistent issues, most major ISPs will start to have you flagged as spam almost immediately.
Why “550” Errors Impact Performance
One of the most common SMTP errors is the “550 Requested action not taken” bounce. Usually due to bad/ no emails, blocked domain or if there’s a filter for being too spammy, the “550” error will cost you efficiency. When an email bounces “550,” it’s bad list hygiene and immediately, your deliverability takes a hit because the number of “550” messages received is an indication of bad form. Also, always throwing “550” errors will hurt sender reputation. When ISPs no longer believe a sender, they are simply less likely to allow those next emails into an inbox and this also can have the effect of lowering the open rate for a campaign.
Why Sender Reputation Relies on SMTP Errors
Any kind of permanent SMTP error is bad for sender reputation; therefore, SMTP errors are an important factor in sender reputation. The more you cause an error, the more ISPs start raising eyebrows. Sender reputation determines whether or not ISPs will block/filter/send your messages inbox placement rates are important for sender reputation. If the sent reputation exists that’s compromised because of the errors sent, mailbox placement rates will drop further if ISPs find any reason to believe bad practice is in place even if it isn’t and is just an error in your sending practices.
Why Campaign Analytics Suffer from SMTP Errors
SMTP errors impact campaign analytics because they create inaccurate assessments of deliverability, open rates, and engagement. For example, consistent SMTP errors create high levels of bounce which get factored into overall deliverability results. But this isn’t fair, for SMTP errors do not indicate bad engagement or interest so why should these numbers be used to compound other factors? Misleading bounce percentages or driven results complicate the ability to assess campaign performance metrics because it’s impossible to adjust when metrics are complicated even when it was a forced error from SMTP.
How to Avoid SMTP Errors
Avoiding SMTP errors comes with prevention and diagnosis. For example, by cleaning lists frequently to ensure valid and not out-of-date email addresses, this avoids permanent errors. Diagnosis comes in the form of server responses for real-time understanding and troubleshooting. Regarding transmission errors, acknowledging that something has gone wrong and adjusting accordingly in the moment prevents temporary SMTP errors from becoming permanent ones and more serious issues.
Improving Your List Hygiene to Avoid SMTP Errors
Companies that have better list hygiene end up with fewer SMTP errors. For example, when one regularly cleans bounced addresses, typographical errors, and people who haven’t opened emails in a long time, there’s proper list hygiene. When all email addresses are verified, it’s almost guaranteed that only valid sending will occur, avoiding permanent SMTP errors. This means successful email delivery while maintaining a good sender reputation for future sends and access to the highest quality results for successfully situated email marketing efforts.
How Analytics Can Help Identify SMTP Errors Before It’s Too Late
Analytics can ensure that after enough data is compiled from past emails sent, marketers can use analytics to see certain patterns that could mean SMTP errors are happening on their end or elsewhere. For example, if a bounce rate is suddenly increasing or deliverability analytics are decreasing at a rapid rate, it could show that someone’s IP or domain is blacklisted or that improper list management is occurring. By using this information to diagnose SMTP issues too many prominent issues coming from one specific email address or domain marketers can fix the problem sooner rather than later instead of waiting to have successful outreach campaigns ruined.
Prevention and Internal Resolution of SMTP Errors Start With Team Training
Your marketing team should be trained on SMTP error prevention and internal resolution if the error is something that can be avoided from an internal perspective. When they know common error codes and what they mean, next steps to prevent or alleviate errors empower them to take initiatives to stop/control the situation with email deliverability. In addition, continuous training ensures better standards for emails, a better sender reputation, and better current campaign momentum for future successes in email marketing.
Solve SMTP Errors Quicker With ISP Communication
If SMTP errors become consistent due to the same situation, troubleshooting with an ISP can solve SMTP errors quicker. Part of using an ISP is cultivating a relationship; when ISPs see that you are taking their information and quickly addressing it with prompt feedback, they see that you’re acting in good faith. Thus, collaboration helps alleviate quicker SMTP issues. In addition, communication helps identify how you’re sending and the possible risk; sometimes a conversation will lead to solutions that wouldn’t even be pinpointed without dialogue. This strengthens sender reputation and opportunities for deliverability for future campaigns.
Prepare To Avoid SMTP Errors For Future Email Campaigns
Ultimately, the sooner you can implement actions to rectify your current campaign strategies/errors, the easier it will be to avoid SMTP errors in the future. Preparation to avoid SMTP errors in the future includes strict compliance with authentication protocols, email validation on the sender end, and changing sending habits based on analytics recommendations. When senders practice best practices over time while getting ahead of what ISPs want from the start, they will see improved deliverability, a better sender reputation, and a strong campaign that lasts.
How Email Authentication Protocols Can Help Reduce SMTP Errors
Implementing email authentication protocols like SPF, DKIM, and DMARC helps reduce SMTP errors. These protocols essentially verify sender identity, meaning there’s less of a chance that the message is marked as spam or rejected on the receiving end. When brands ensure that they have these verification systems in place and assess and change them when and if necessary they benefit from lower SMTP rejection rates, maintained sender scores, and improved overall deliverability, all of which enhance email marketing efforts for performance and credibility.
The Advantage of Analyzing SMTP Errors to Become Aware of Patterns
Analysis of SMTP errors allows marketers to assess errors and find patterns that help them respond to future occurrences at the source. For example, if one team consistently gets high errors working with a certain domain or through a specific server, in the future they can take that information and either avoid that course of action or better predict problem sends. By analyzing SMTP response codes received over time, it’s easy to see if there are consistent errors in a certain area and make adjustments for better sends, more deliverability, and less disruption to successful campaign efforts since behaviors can be learned and adjusted moving forward.
The Dangers of Avoiding SMTP Error Intervention Over Time
Avoiding intervention for SMTP errors will create negative implications for email marketing efforts over time. While a one-time occurrence of an email being rejected may feel like it’s just an error that won’t happen again, in reality, if this happens on a larger scale over time, decreased deliverability is imminent, loss of follow-through, and potential to be blacklisted by larger ISPs. Over time, these consequences add up to create less effective campaigns with no reach and poor return on investment. This can easily be avoided by addressing errors as they happen and utilizing SMTP error management strategies preemptively.
Conclusion
The relevance of recognizing SMTP errors and what they mean comes from the need for effective email marketing in an age where email is one of the more prominent forms of communication and marketing to reach and engage with an audience. SMTP errors occur as many error codes live within a server that can acknowledge a problem after an email has been attempted for delivery. There are temporary problems email gets queued for various reasons (server overload is a common one) and permanent problems emails that cannot be delivered because of typos in the address, unregistered domains, or being sent to spam. These are just a few reasons why marketers need to understand the kinds of SMTP errors that occur, for they can severely impact campaign deliverability, sender reputation, and audience engagement.
SMTP errors are controllable as long as they’re monitored and caught early on; marketers must frequently analyze the responses from the server in question to understand the evolving problems. For instance, SMTP errors are permanent or temporary, and compiling a list of various SMTP error codes can help marketers pinpoint which codes are active sooner rather than later domains that the sender is using are blocked, or mailboxes are over quota. When SMTP errors are caught early on, they can be remedied before they become larger problems. For example, an uptick in bounced emails due to invalid email addresses will hinder campaigns with set publish dates if not caught early. Over time, sender action will negatively impact them with ISPs who will mark them as spammers and reduce their opportunities in inboxes; therefore, the sooner marketers’ teams can detect problems, the better they can remedy them without impacting the anticipated campaign timelines.
In addition to catching errors at the onset, good list hygiene can maintain and prevent SMTP errors before they occur. Invalid email addresses that remain in inboxes due to poor upkeep or improper formatting can ruin sender reputation, leading to permanent SMTP errors that impact deliverability but not quality. Additionally, good authentication practices posited by marketers and followed through by consumers SPF, DKIM, DMARC enable ISPs to authenticate proper ownership and good intent behind the email address which allows for SMTP error response before rejection as presumed spam.
Finally, there should be consistent education for any email marketing team about SMTP errors so that intervention can happen should any coding appear. The more educated a person on the team is about SMTP error codes and why they happen, how to eliminate them the better chances to positively intervene exist before performance is hindered. Ongoing education fosters a cumulative history of knowledge that easily defers potential problems sooner rather than later.
Ultimately, knowing how to detect SMTP errors early, how to prevent them, and how to solve them only enhances engagement going forward, ensures accurate reporting mid-campaigns, and secures email marketing success over time by being able to keep sender reputations in their integrity. Prevention occurs through proactive measures using information for effective solutions instead.
Tech
The Power of Digital Marketing for Business: A Guide to Maximizing Your Reach


Digital marketing has become an essential tool for modern businesses. It involves using the internet and online technologies to connect with potential customers. This form of marketing is cost-effective and allows businesses to reach a wider audience compared to traditional marketing methods. In today’s digital age, businesses cannot afford to ignore the power of the internet. Companies that use digital marketing strategies are more likely to thrive in a competitive market. By promoting products and services online, businesses can increase their visibility, attract more customers, and boost their overall sales. Digital marketing includes various tactics such as social media, SEO, email marketing, and content creation. Each of these strategies works together to help a business connect with the right audience. With digital marketing, businesses can interact with customers directly, build stronger relationships, and encourage loyalty. As a result, businesses can expect better returns on their investments. Digital marketing allows companies to track their efforts and see which strategies are most effective. This helps businesses make informed decisions about their future marketing strategies. Ultimately, digital marketing helps businesses grow by increasing their online presence, generating more leads, and improving customer engagement.
What is Digitari and Why It Matters
Digitari is a platform that offers a wide range of digital marketing services designed to help businesses thrive in the online world. Whether you’re a small startup or an established company, Digitari provides the tools and expertise needed to grow your business. With a focus on digimarkkinointi yritykselle, Digitari uses advanced strategies like SEO, social media marketing, and online advertising to drive success. One of the key features of Digitari is its ability to create customized marketing plans based on the unique needs of each business. This means that businesses get a personalized approach that targets the right audience. Digitari also provides detailed analytics, allowing businesses to measure the effectiveness of their marketing campaigns. With this data, businesses can optimize their strategies and improve results. This ability to track progress and make adjustments is a crucial advantage in the fast-changing digital landscape. Moreover, Digitari helps businesses stay ahead of the competition by implementing the latest digital marketing trends. By using the right tools and resources, Digitari ensures that businesses maximize their online presence and reach their target audience more effectively. This is why Digitari is an essential resource for any business looking to grow and succeed in the digital world.
Key Benefits of Digital Marketing for Business
Digital marketing offers businesses several key advantages that can lead to significant growth and success. First, digital marketing helps businesses reach a global audience, which is impossible with traditional marketing methods. It breaks down geographical barriers, allowing businesses to market to people across the world. Secondly, digital marketing is more cost-effective than traditional advertising methods. For example, running an online ad campaign can be much cheaper than paying for TV or radio commercials. Additionally, digital marketing offers targeted advertising. This means businesses can direct their marketing efforts towards a specific group of people based on their interests, location, or behaviors. As a result, businesses can avoid wasting resources on people who are unlikely to be interested in their products or services. Another major advantage is the ability to measure results. Digital marketing tools provide businesses with detailed analytics, allowing them to track the success of their campaigns and make adjustments as needed. Furthermore, digital marketing allows businesses to engage directly with their customers through platforms like social media and email. This helps build stronger customer relationships and encourages loyalty. By leveraging these advantages, businesses can maximize their marketing efforts and achieve greater success.
- Global Reach: Digital marketing allows businesses to reach a global audience.
- Cost-Effective: Compared to traditional marketing, digital marketing is more affordable.
- Targeted Advertising: Digital marketing enables businesses to target specific customer groups.
- Measurable Results: Businesses can track and analyze the effectiveness of their campaigns.
- Direct Engagement: Digital marketing fosters direct communication with customers, improving relationships.
Digital Marketing Channels for Businesses
There are several channels available for businesses to use in their digital marketing strategies. One of the most important is Search Engine Optimization (SEO), which helps businesses improve their visibility in search engine results. By optimizing their website and content, businesses can attract more visitors and increase their chances of generating sales. Another key channel is social media marketing, where businesses can engage with their audience on platforms like Facebook, Instagram, and LinkedIn. Social media allows businesses to share updates, respond to customer inquiries, and promote products or services. Email marketing is another powerful tool that businesses can use to reach customers directly. By sending personalized emails, businesses can keep their customers informed about new products, promotions, or special offers. Pay-per-click (PPC) advertising is also a popular method, where businesses pay for ads that appear in search engine results or on other websites. Finally, content marketing involves creating valuable and relevant content, such as blogs, videos, or infographics, to attract and engage customers. When used together, these channels form a comprehensive digital marketing strategy that helps businesses reach their goals and connect with their target audience.
The Role of Digitari in Enhancing Digital Marketing
Digitari plays a crucial role in helping businesses improve their digital marketing efforts. One of the main advantages of using Digitari is its ability to create customized digital marketing strategies for each business. This ensures that marketing efforts are tailored to the specific needs and goals of the business. Additionally, Digitari provides detailed analytics that helps businesses track the performance of their campaigns. By analyzing this data, businesses can identify what is working and what needs improvement. Another key benefit of using Digitari is its expertise in SEO and PPC. Digitari helps businesses optimize their websites to rank higher in search engine results, making it easier for customers to find them online. It also manages PPC campaigns to drive targeted traffic to a business’s website. Furthermore, Digitari offers content marketing services, creating high-quality content that attracts and engages customers. With its extensive knowledge of digital marketing, Digitari ensures that businesses stay ahead of the competition and make the most out of their marketing budget. Overall, Digitari helps businesses enhance their digital marketing strategies, leading to increased online visibility, better customer engagement, and higher sales.
- Customized Strategies: Digitari creates personalized digital marketing plans.
- Comprehensive Analytics: It provides detailed data to help businesses track their success.
- SEO and PPC Services: Digitari optimizes websites and manages paid ads.
- Content Marketing: Digitari creates valuable content to attract customers.
How to Get Started with Digital Marketing for Your Business
Getting started with digital marketing can seem challenging, but it becomes manageable if you break it down into simple steps. The first step is to define your goals. Ask yourself what you want to achieve with your digital marketing efforts, such as increasing website traffic, boosting sales, or building brand awareness. Next, choose the right digital marketing channels for your business. You might want to focus on SEO to improve your search engine ranking or social media marketing to connect with customers directly. Once you’ve selected your channels, the next step is to create high-quality content that appeals to your target audience. This content could be blog posts, videos, or social media posts. After publishing content, monitor the results. Use tools like Google Analytics to track the performance of your campaigns and see what’s working. Finally, consider working with a digital marketing expert like Digitari to help you navigate the complexities of online marketing. They can guide you through the process and ensure your business is using the best strategies for success.
- Define Your Goals: Set clear objectives for your digital marketing efforts.
- Choose the Right Channels: Select the best digital marketing channels for your business.
- Create Quality Content: Develop content that attracts and engages your audience.
- Monitor Results: Track the success of your campaigns using analytics tools.
- Consider Professional Help: Hire experts like Digitari to guide your marketing strategy.
Common Mistakes to Avoid in Digital Marketing
While digital marketing offers great opportunities, many businesses make common mistakes that can hinder their success. One of the most significant mistakes is neglecting mobile optimization. With more people using smartphones to access websites, it’s crucial that your website is mobile-friendly. Another mistake is not using data analytics to measure the effectiveness of your campaigns. Without tracking results, businesses miss out on valuable insights that could improve their marketing strategies. Ignoring SEO is another common error. SEO is essential for driving organic traffic to your website, and without it, your online visibility will be limited. Inconsistent branding across different platforms can also confuse potential customers. It’s important to maintain a consistent voice, look, and feel on your website, social media, and ads. Finally, some businesses fail to update their marketing strategies regularly. Digital marketing trends change quickly, so it’s essential to stay current and adapt to new technologies and practices. By avoiding these mistakes, businesses can improve their digital marketing efforts and achieve greater success.
Conclusion
In conclusion, digital marketing has become a vital part of any business’s strategy for growth. By using platforms like Digitari, businesses can create customized marketing plans that help them reach their target audience and achieve their goals. The key benefits of digital marketing include global reach, cost-effectiveness, and the ability to track and measure results. By using the right channels and strategies, businesses can improve their online presence, increase engagement, and boost sales. It’s essential to avoid common mistakes and stay updated on the latest trends in digital marketing. Whether you are just starting or looking to improve your existing efforts, digital marketing provides endless opportunities for businesses to grow and succeed in the digital world. Embrace the power of digital marketing and watch your business thrive.
Tech
The Role of Headless CMS in Managing Large-Scale Documentation Systems


However, as businesses grow and the amount of documentation increases, sifting through massive amounts of documentation can become increasingly tricky. Businesses need to meet a diverse user base and multichannel access consistently with accurate documentation that meets time and access challenges. Headless content management systems (CMS) provide a revolutionary means of streamlining such endeavors for large-scale documentation management. With its separation of the creation element from the eventual presentation and delivery aspect, headless CMS solutions provide the best in flexibility, extensibility, and efficiency. This article explores how headless CMS effectively manages large-scale documentation systems.
What is Large-Scale Documentation?
Large-scale documentation refers to generally large collections of information about many topics or many products/services. Such information collections must be organized precisely, consistently displayed in proper design and format across various channels, and accessed quickly. Yet many CMS systems fail to provide this access due to unintuitive navigation, overwhelming usage for scalability, and ineffective updating that keeps previously vaulted information live and difficult to find. Sanity open source alternative platforms offer a more flexible and customizable foundation for handling large-scale documentation, with structured content models and developer-friendly tools that enhance both scalability and usability. Yet a proper documentation management system requires a proper structure/infrastructure and rendering capabilities; thus, the advent of headless CMS architecture allows users to more easily sidestep typical documentation management concerns.
How Does Headless CMS Ease Content Organization?
The most crucial element associated with large-scale documentation is content organization. When large, unwieldy collections of information are out of order or difficult to navigate, the whole system is unusable. Regardless of project scale, headless CMS solutions make content organization easier because they compartmentalize information on many levels. In addition to vast taxonomies and customizable classifications, headless CMS separate presentation from the management layer. Therefore, content teams can create hierarchies without concern for how it will look on the other side of the publication process.
What Allows for More Efficient Workflow Management for Documentation?
Documentation is what projects are based around, which means time dedicated and concern related to keeping information correct, updated, and useful is paramount. The more extensive the documentation allows it to be, the easier it is for teams to forget when to update content or when it’s ready to publish. Headless CMS allows for more efficient workflow management for documentation with project-specific tools-included functionality such as collaborative editorial projects, access rights by role, and in-line comments. Content contributors can collaborate with each other, and Projects IT is involved at the beginning whenever content elements are needed beyond text. Furthermore, features and tools being easily found increases rapid administrative whitespace time between efforts for republishing, decreasing drop-off between version one and version two.
Supporting Multi-Channel Documentation Delivery
Many companies host their documentation on various channels, from websites to mobile applications to portals and even voice-activated devices. A headless CMS encourages multichannel offerings, as it can provide the documentation via cross-functional APIs. Therefore, companies can rely on the necessity of a unified documentation experience. If the same documentation appears in different places, providing users with the appropriate access to understand it better and offering a uniform experience, then it can be done and ensured. No matter how or where users interface with the company, they will receive the proper, consistent information they need. Multichannel offerings for external documentation efforts improve satisfaction, reach, and usability.
Ensuring Consistent Updates Across Documentation Accuracy
When large documentation efforts exist, there needs to be consistent elements of content across all endeavors. A headless CMS allows for consistent content updates through version control, revision history, and audit trails. Therefore, if users make mistakes, they can go back and see where they went wrong to adjust instead of starting anew. Furthermore, content can be delivered through the API instantaneously to maintain consistency across documentation as well. Thus, anyone working on the headless CMS will have access to the most current pieces instead of relying on old versions sent via email or downloaded on their computer. This consistency reduces confusion for end-users while improving trust and authority across the enterprise.
Improving Performance and Efficacy for Scalable Efforts
As stated throughout this piece, performance matters for large enterprises looking to scale their documentation offerings. A headless CMS improves performance via caching, content delivery networks (CDNs), and more robust cloud-based infrastructures. This results in less loading and less demand for high-pressure use with many users actively using a giant library simultaneously. The effectiveness of headless CMS architecture allows for seamless scaling, meaning that even if an entirely new library arrives overnight, performance will stay consistent and high-quality without stress.
Increased Search and Discoverability for Documentation
If documentation is searchable, it’s usable. Many headless CMS options involve integration with top-tier search technology and in-software search and find capabilities that are quick, accurate, and able to reach even the most hidden depths of content storage in large-scale systems. In addition, headless CMS options involve content modeling and easy-to-assign metadata and taxonomies that improve discoverability as well. The easier it is to find what’s needed in documentation, the better the experience less frustration, more ease of finding what’s needed is crucial for success.
Ability to Assess Usage and Improve Documentation Over Time
Large-scale documentation requires systems of continuous improvement for long-term effectiveness. Many headless CMS options involve integration with systems that can track usage, such as known analytics systems that get adopted by libraries of documentation, content usage and performance, and advanced capabilities for search and discoverability. With such information, large-scale organizations can see areas where proper documentation isn’t enough, how some information is relevant and needed, and others, overlooked and unnecessary, as well as the overall structure of documentation to better define results. Use of analytics in the development of long-term improvements for documentation ensures accuracy, contentment, and effectiveness over time.
Enhanced Collaboration Across Various Teams
Large-scale documentation efforts commonly mean that those creating the content aren’t necessarily in one central, located team. Whether due to remote work across the organization or a multinational presence in various cities and time zones, large-scale documentation efforts need collaboration from various teams. Headless CMS options allow for enhanced collaboration through due dates, assigned projects that don’t overlap across various teams working on the same initiative, and edit/comment capabilities within documentation areas if a project passes through someone else’s dedicated hands. Better collaboration allows for better operational efficiency as large-scale efforts won’t suffer because many hands are in the pot.
Solving the Implementation Problems, but Not Completely
Unfortunately, where advantages exist in employing headless CMS platforms, organizations must remain wary upon implementation in terms of technicality, resources, and integration needs. The need for proper implementation and strategic operation requires an in-depth knowledge of all trained personnel on staff as well as any expert technical partners. Complications must be managed to ensure that organizations receive all the benefits a headless CMS can offer without too much disruption to existing operations and processes as it is business as usual.
Improved Security and Compliance Features
Security and compliance features are necessary when it comes to any major documentation system. The infrastructure of a headless CMS enables higher level security features from secure API authentication to role-based access controls, encryption, and logging. This not only protects sensitive data from prying eyes and minimizes access for anyone other than necessary users, but ensures compliance capability with different regulations that demand strict standards (GDPR, HIPAA). Security creates trust and dependency for users who need to believe their access to documentation is reliable information.
Headless CMS & Large Scale Documentation and the Future
The future of using a headless CMS to manage large-scale documentation will only get better. With integration into AI, machine learning, and other growing technological elements, organizations can look forward to automated documentation prompts, improved tagging capabilities for content, and personalization of information provided. Furthermore, speech-to-text for documentation, digital assistants, and proactive, real-time support will transform the way people work with documentation systems. Organizations that integrate headless CMS will be ahead of the game to match the growth potential of future benefits, ensuring that down the line, they will never be at a competitive disadvantage for integrating this technological system.
Increasing Usability with More Personalization
Dynamic personalization is what drives successful enterprise documentation systems as it provides content delivery based on exact needs and situations determined. A headless CMS environment allows enterprises to plug in personalized experiences based on user role, profiles, or case use. Those who access enterprise-level documentation systems are much more likely to see only what’s relevant to them, directed toward them, which automatically allows better navigation through an expansive enterprise archive. This level of personalization increases engagement and satisfaction and decreases time spent searching for essentially already known information.
Reducing Costs of Operations with a Headless CMS
One of the increasing cost factors comes from sustaining an enterprise-level documentation system. A headless CMS can reduce operational costs by a staggering amount as it creates efficiencies in maintaining documentation systems and automated integrations of all documentation tasks. For example, using an API to oversee a large-scale documentation approach limits redundancy in action as it requires less hands-on interaction (and mistakes) while reducing resource output. With a better-oiled machine running, it’s clear an enterprise has lower costs associated with documentation management without compromising quality.
Making Documentation Systems Future Proof with a Headless Architecture
In the long run, using a headless CMS will ensure that enterprises can implement future developments and improvements down the line as well as gradual changes in market demand of users. Separating the backend content management from front-end presentation allows for updates to occur over time, integrating future trends such as AI, chatbots, voiceover assistants, and augmented reality into the documentation experience. Thus, enterprises remain competitive over time with a headless CMS solution that allows their documentation systems to intrinsically adapt to best serve future ideas and practices.
Conclusion
Headless CMS platforms are critical for large scale, complex documentation systems because they expedite and simplify management. As organizations age and repositories become more extensive, the problem is ensuring everything remains accurate, readily accessible, and updated consistently. A traditional CMS will not suffice; the requirements for today’s standards in user assessment, outreach, and the speed of documentation updates exceed what a regular CMS can provide. A headless solution inherently supports such construction, as it decouples back-end content creation from front-end delivery, allowing for greater customization, scaling, and flexibility based on user needs.
For complex systems of architecture with thousands of organizational possibilities for content, a headless approach provides all the management tools needed to keep everything in check successfully. For example, more complex taxonomies, regular metadata volumes, and complicated content modeling features can make even the most complex documentation system clear and concise. Improved features like searchability come from consistently applying metadata across all assets via the headless CMS back-end. Furthermore, content management capabilities can simplify processes, like specialized workflows with approval chains, requirement updates for aging content, and notifications. These promote productivity for operational teams constantly assessing many assets. For time-sensitive documentation systems needing a lot of additional focus, a headless approach works best because team members can communicate through a cohesive back-end interface for further granular clarity on who has what access.
Distributing access across multiple channels is easy when version control is not an issue from the start. APIs allow for easy distribution to different access points web, mobile, voice and clients receive the same version no matter if delivered on a mobile app or via the desktop voice-activated site. Headless applications use API-driven designs for front-end delivery; whatever channel is used for access maintains the integrity of content and engagement interface, allowing users to be comfortable using the mobile app or voice activation with no concern for information discrepancies.
Search is critical within large systems; thus, the appreciation for a headless experience is all the more vital. Advanced search applications foster discoverability within systems through proper indexing with forms of controls and granular access options. In addition, analytics can impact access and feature determination by assessing what’s most engaged at any given time across organizational hierarchies; headless architectures provide the analytics resources to ascertain this information and adjust features accordingly.
Lastly, organizations seeking solutions to ensure long-term viability and success will be on good footing, particularly because of the strategic flexibilities a headless CMS can offer. With solutions that adjust as new systems come to light over time, organizations can always access documentation opportunities without undermining quality or consistency resulting in constant improvements due to new technology and evolving user expectations, which will further enhance their competitive edge in the marketplace.
-



 Biography7 years ago
Biography7 years agoJacqulyn Elizabeth Hanley is the Mother of Liza Soberano?
-



 Biography7 years ago
Biography7 years agoAmanda Levy Mckeehan Biography, Family, Net Worth, Age, Affairs, Facts
-



 Home6 years ago
Home6 years agoEpson L3110 Driver Free Download Latest Updated Version
-



 Games5 years ago
Games5 years agoBest Free To Play MMORPG To Try This 2021
-



 Biography7 years ago
Biography7 years agoWho is Rose Dorothy Dauriac? Scarlett Johansson Daughter?
-



 Home7 years ago
Home7 years agoLiza Soberano Biography, Age, Family and Boyfriends
-



 Biography7 years ago
Biography7 years agoJessica Ditzel Secret Information that Nobody Knows | Joe Rogan’s Wife
-



 Biography7 years ago
Biography7 years agoWhat is the relation of Nathaniel Larry Osorno with Liza Soberano?